Protecting Passwords for Business

Protecting passwords is a continual process. With the periodic changes in how hackers launch their attacks, changes in how passwords are protected must be a part of the periodic review of security procedures. Fortunately for the website owner/operator, there are a variety of options to consider if better security is their goal.
There are a variety of vendors who offer two-factor authentication systems. For those using WordPress in their Web services offering, one of the options is Google's two-factor authentication system. This can be implemented by installing one or two plugins. The second plugin moves the screen for the two-factor token on a separate screen instead of being on the same screen as the username and password fields. The flexibility comes in when the user is presented a QR enrollment code leaving it to them as to which client software platform that is used to manage the logins. As with any technology, there can be a variety of ways it can be implemented. Google's own implementation using a Web browser provides for more than one hardware key to be used in addition to being able to enter one time keys generated by an assortment of two-factor clients.
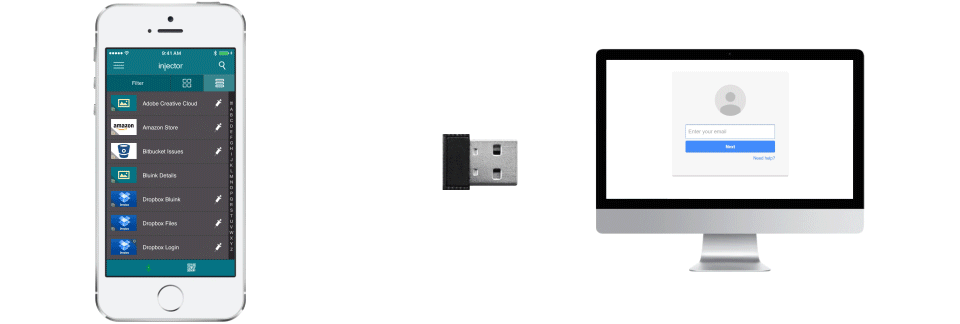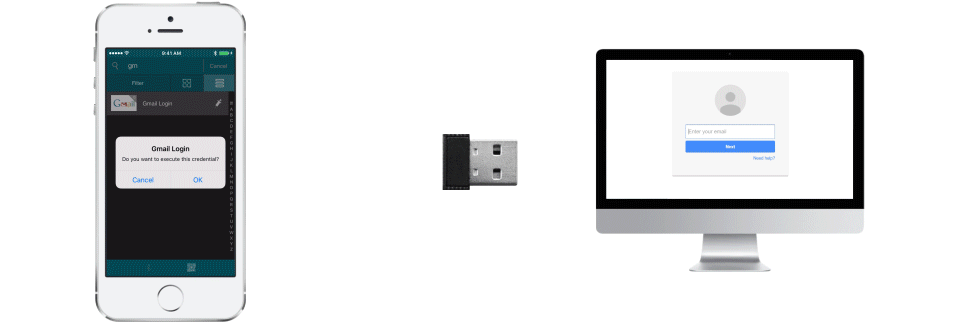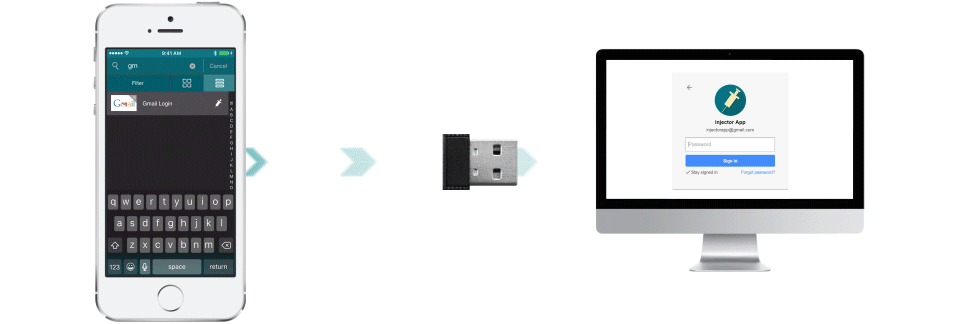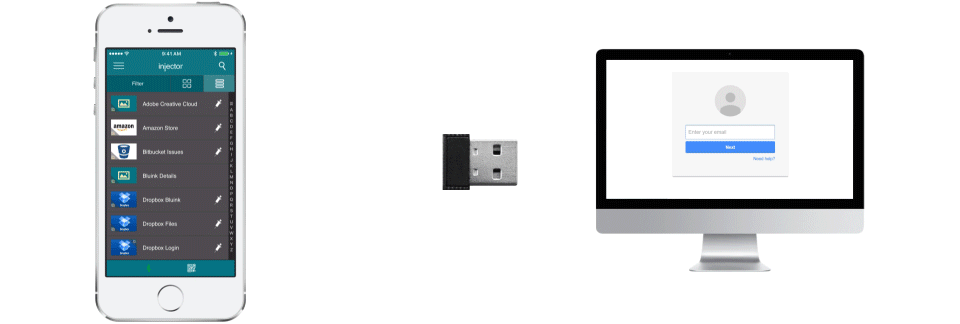
For those who work in situations where they would prefer to avoid any possibility of someone seeing what is being entered for a username, password or two-factor token, Injector offers an interesting solution to the problem. Using a special Bluetooth dongle, a secure connection is established from the smartphone to the computer logging into a particular system/service. After going through an authentication process on the smartphone client, it is just a matter on tapping on the on screen buttons to send the username, password and two-factor token values.
The next iteration in methods of protecting login credentials is available from Clef. It is with this type of protection that the potential for a password-less login environment. To see Clef in action, there is a demo available on the website. Basically, it uses the camera in an enrolled smartphone to authenticate a login to the desired website. The smartphone screen looks like a series of vertical dancing bars that negotiate with the website being logged into. With the current version of the SDK, only one smartphone can be enrolled per login, so a misplace smartphone might present a challenge. Hopefully this will be addressed in a future update.
In some two-factor authentication solutions, using a SMS message to send the code to be entered during the login process has been a popular solution. This may not be the case in the near future. In the current draft of the Digital Authentication Guideline from NIST (National Institutes of Standards and Technology), it is being proposed to not send two factor codes via SMS message. If the use of SMS is to be continued, then additional security mechanisms may need to be put in place depending on what the final version of the publication recommends. Since U.S. government websites generally follow NIST guidelines, they are watching this guide closely. They will be the first to implement the recommendations with the commercial sector probably following soon thereafter.
A technology that is just starting to seen wide-range implementation is Eyeprint ID from the folks at Eyeverify. Eyeprint ID uses the camera in a smartphone to map the blood vessel patterns and other micro features to have the eye be a fingerprint for authentication. While, at this point, not all smartphones are supported, that has already been changing over the past few weeks. This implementation has several benefits over similar technologies in that it doesn't use a low-level laser or led light source to read the eye, it works with existing light source. This should make Eyeverify very attractive to those in Europe which normally have been very cautious of anything using a laser anywhere near the eye. For those who have to wear glasses, the glasses will need to be removed for the current technology to work. Hopefully a way will be found in a future update to not have to remove glasses for this to work.
While no one option will be good for everyone, there are a variety of options that make it easier to provide additional levels of protection. With the improvements in technology that continue to come to market, it is reasonable to expect improvements to existing offerings in addition to new to market solutions.
About the Author
Ronald Nutter is a Best Selling Author and Speaker. He has published a book "The Hackers Are Coming... How-To Safely Surf The Internet". You can learn more about this book at https://www.ronnutter.com/kpyop. It is available in both Kindle and paperback formats.
Subscribe to Our Newsletter!
Latest in Software








